Remember the
good old days...
...when the data
center was under your roof...


...and you knew
the people in your
LDAP or Active Directory...
That was then.
This is now.
Welcome to the Age of the Cloud.
Now, who ARE all those people in your network...
Suppliers and
distributors...?


Contractors...?
"Customers..."?

Call it cloud computing, call it pervasive outsourcing and work-from-anywhere; the fact is that your infrastructure has changed.
 But the assumptions behind security products and protocols are stuck in the days when “on the network” meant “in the physical building.” That’s why Tanium and others
are calling out the naked security emperor in full-page Wall Street Journal ads.
But the assumptions behind security products and protocols are stuck in the days when “on the network” meant “in the physical building.” That’s why Tanium and others
are calling out the naked security emperor in full-page Wall Street Journal ads.
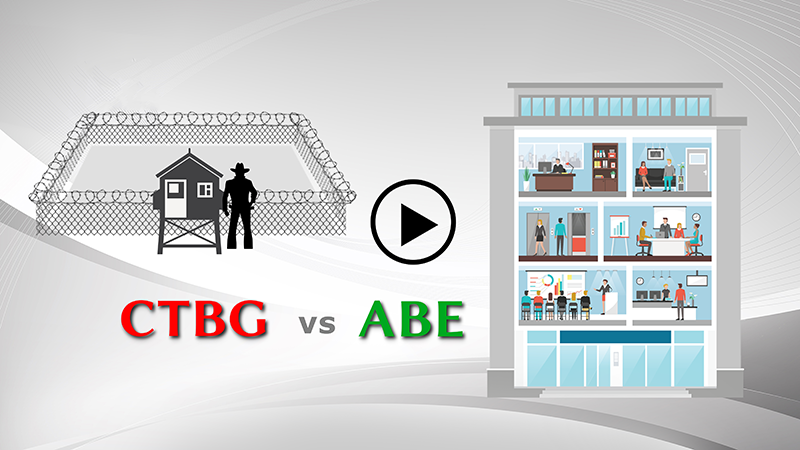
CTBG lingers long past its expiration date Catch
The
Bad
Guys
Obsolete CTBG assumptions linger in the design of security products and protocols. CTBG assumes that it’s possible to determine the intentions and character of the sender of a stream of bits.
Isn’t that like asking your building’s lobby receptionist to determine the intentions and character of everyone who walks through the door? Would that work?
Of course not. Instead, you tell the receptionist to ask the visitor for some form of identity credential, then issue a visitor badge. REAL security is about environments of accountability; it’s not about catching bad guys.
ABE will bring REAL security to your infrastructure
Accountability
Based
Environments
These days, your network is replacing your buildings. A widely dispersed collection of people with whom you never rub shoulders are in there, looking at files and installing software.
You need to know with a reliable measure of certainty just who those people are.
It’s time for ABE (Accountability-Based Environments). ABE ensures every network interaction is secure and accountable. It’s not just about spotting threats; it’s about knowing exactly who’s accessing your data and why.
Let ID4Cloud introduce you to solutions based on ABE assumptions to secure your cloud and ensure every user is authorized and accountable.
ID4Cloud introduces you to solutions that let you know who's in your network, touching your valuable information assets.
Identity used to be a rather simple matter. Personnel records from HR went into your LDAP or Active Directory and were managed by your identity management software. You knew who your people were because you saw them face-to-face every day.
Now, your users come from remote offices and suppliers and distributors and customers. Who checked the identities of these people? How sure are you that they are who they say they are?
Indeed, how sure are you that your competitors haven't taken advantage of the vague and variable ways that identities are claimed out there in the wild?
Now you can have measurable certainty
of the identities of your remote users.
Let us show you how the IDQA™ system (IDentity Quality Assurance) lets you and your relying parties know with measurable certainty the reliability of a claim of identity.